It’s like something out of a spy movie. Federal agents swooped down on a Chinese-born former Apple (AAPL) engineer as he boarded a flight for China. Other agents pounced on another Chinese-born engineer as he hot-footed it for the airport. The men are suspected of stealing the secrets of Apple’s self-driving car project.
A search of one of the suspects’ homes turned up a laptop at the bottom of a laundry hamper, a laptop that contained trade secrets about ethernet technology belonging to another company, chip supplier Marvell Technology Group (MRVL). Another search found a classified document related to Raytheon (RTN)’s Patriot missile program.
On Monday, lawyers for Apple told a court that the company has “deep concerns” the suspects will try to flee before their trials. The men were each charged with one count of criminal trade secrets theft. They pled not guilty, and nothing has been proven.
Still, to knowledgeable observers, it looks like another incident in the conflict at the heart of the show-down between Washington and Beijing that I talked about last week: The Tech War.
Technology is the second front of “The China Dream” for global domination, and it’s based on Secret Code #5 …
Steal your opponent’s ideas and technology.
OR: Theft is an easy, cost-effective way to usurp power from your adversary.
American politicians from both parties basically left the door wide open … for decades. Not much “sneaking” or “stealing” necessary.
Even so, the Chinese were willing to steal behind America’s back …
For example, Chinese engineer Dongfan Chung worked on the B-1 bomber, the space shuttle and other projects. In 2010 he was sentenced for spying in support of China’s aviation industry. Investigators searched his home and found 250,000 pages of sensitive documents. God only knows how much intel he passed to Chinese officials between 1979 and 2006.
But the Chinese wanted more. So they turned to cyber espionage.
China is the primary source of cyber spying against the U.S., and it allows the Chinese to cheat their way up the technology ladder … mostly via intellectual property theft and forced technology transfer from companies that do business with China.
In support of its ironically-named “Made in China 2025” policy for dominance in 10 strategic high-tech sectors …
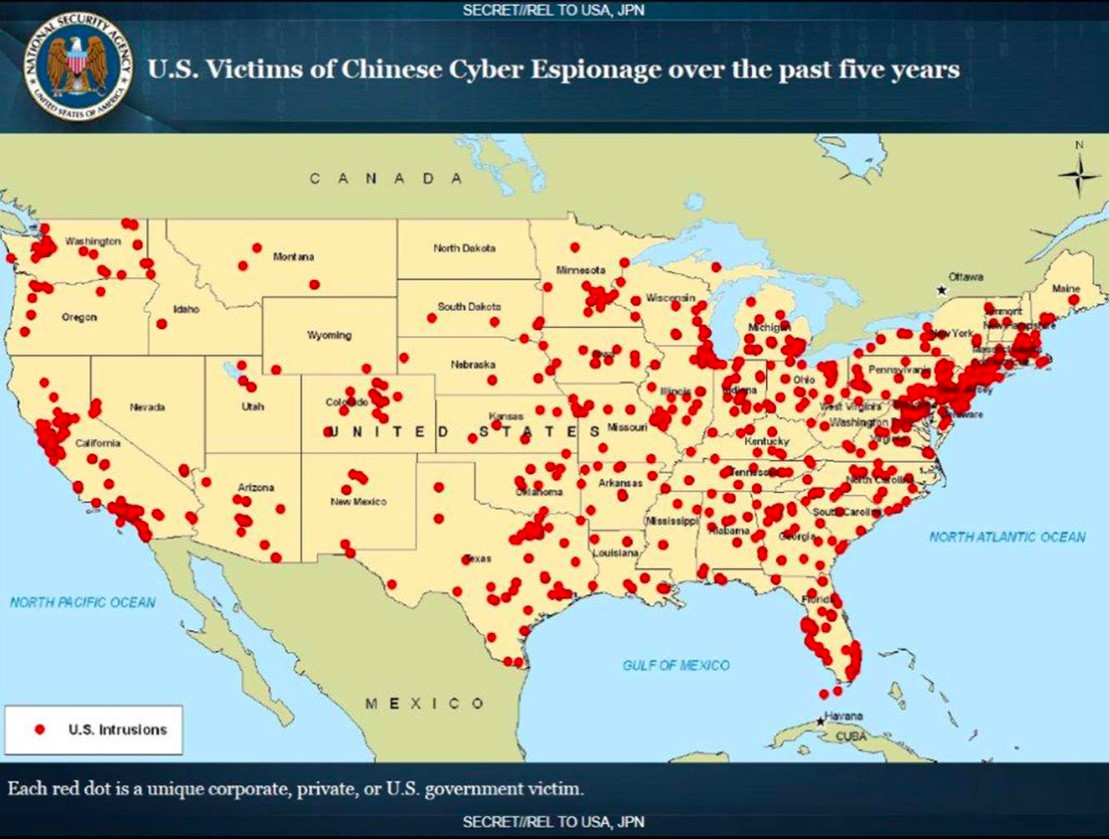
Chinese hackers regularly infiltrate American corporations, academic institutions, research organizations and more. Victims include Alphabet (GOOGL), AT&T (T), the U.S. Chamber of Commerce, Visa (V), Mastercard (MA) and even the Departments of Defense, State, Homeland Security and Energy! Here’s a map showing Chinese hacking attacks over a five-year period.
Notice the concentration of cyberattacks against technology targets in San Francisco, financial targets in New York and military-intelligence targets around Washington, DC.
To evade detection, China uses ever-evolving tools: malicious software … hacker proxies … even rerouting of cyber ops through third (or fourth) countries.
Hacking is central to China’s 100-Year Marathon to steal technologies it can’t invent and intellectual property it can’t create.
The Commission on the Theft of American Intellectual Property found that theft of intellectual property likely costs our economy more than $300 billion per year, including an estimated loss of $107 billion in additional sales annually … and 2.1 million U.S. jobs.
In a speech to the National Association of Manufacturers, Thomas Boam, a former minister counselor at the U.S. embassy in Beijing, alleged that a staggering 10% to 30% of China’s GDP is founded on pirated and counterfeited products.
By some estimates, pirated and counterfeit goods based on Western products now account for 15 to 20% of retail sales inside China. In some locales, the share could approach 90%!
It’s no surprise China’s plan has been characterized by the U.S. Chamber of Commerce as “a blueprint for technology theft on a scale the world has never seen before.”
One Chinese company serves as the perfect case study: Huawei Technologies.
It’s one of largest telecom companies in the world, and major U.S. corporations —even U.S. government agencies and military services — will likely employ Huawei’s global networks.
What’s truly scary is that the company appears to be joined at the hip with Chinese intelligence. Which leads Michael Pillsbury, director of the Center for Chinese Strategy at the Hudson Institute, to wonder …
Could Chinese spy services monitor or reroute certain lines of telecommunications? Could they use these networks to steal information? Could they create ‘kill buttons’ during a future emergency, blocking crucial international network traffic?
For years, American officials assumed all this was just a passing phase, blind to the larger tactics inspired the “secret codes” of China’s Warring States period … and unhindered by constitutional (or moral) constraints.
But now, the U.S. Justice Department is taking action, accelerating prosecutions as part of the Trump administration’s crackdown on China.
In the 10 months leading up to August 2019, the Justice Department brought charges in at least seven economic espionage cases, up from three during the prior 10 months.
Also in August, the Justice Department indicted a University of Kansas researcher on fraud charges for concealing his ties to a Chinese university while working on a U.S. government-funded research project.
The surge in prosecutions is part of the “China Initiative” launched last November by then-Attorney General Jeff Sessions.
The focus of the China Initiative is economic espionage. But it is also identifying corruption involving Chinese companies that compete with U.S. counterparts … implementing new rules for Chinese and other foreign investors in U.S. companies … and applying the Foreign Agents Registration Act to anyone seeking to advance China’s political agenda in the United States.
John C. Demers — announcing an indictment against two players in the theft of turbine technology from General Electric (GE) — said this:
“The indictment alleges a textbook example of the Chinese government’s strategy to rob American companies of their intellectual property and to replicate their products in Chinese factories, enabling Chinese companies to replace the American company first in the Chinese market and later worldwide.”
But regardless of whether the technology is stolen or self-invented, Chinese tech firms are becoming real competition on the global stage. And that’s exactly what China is aiming for: Global technological dominance.
This is a position the U.S. has held securely for a while now. But next-generation tech, like 5G and artificial intelligence, could upend the playing field. If China can get there first, that is.
AI supremacy is of particular concern to many national security experts. AI-enabled drones could revolutionize military conflicts and remove any advantage in size the U.S. military might have. Additionally, AI-enabled hacking programs would pose a serious threat to secure information.
And we’ve all seen the implications of a coordinated cyber disinformation campaign. An AI-enabled program could do significantly more damage.
But we can’t just put up an Iron Curtain. Detangling and separating all intel would hurt the U.S. just as much as China. Like the internet in its early days, the significance of the technology currently in development is so intense, it’s hard to see just how it’ll affect things. But closing off the U.S. from potential developments would leave us out in the cold.
So, where does this leave us on the second front of this New Cold War? On a very precarious precipice.
Keep an eye on your inbox this coming Tuesday. We’ll look at the third front in this new cold war with China: The Geopolitical War.
In the meanwhile, did you know we’re offering a special trial membership to my monthly newsletter, Wealth Megatrends? A 90-day subscription is only $9.95.
All the best,
Sean